DHANASHREE
KOLHE
Zero Trust - URM
I was User Experience design owner for IBM Security MaaS360's User Risk Management (URM) section. Responsible for constant improvisations based on customer feedback. Design representative in org-level innovation sync ups.
Recognitions




To combat this threat organizations have to look across the attack surface for vulnerabilities. And now more than ever, IT teams are ramping up the adoption of unified endpoint management (UEM) solutions like IBM Security MaaS360 with Watson to secure their inventory of all devices and endpoints while ensuring that employees remain productive. Conventional UEM services address security and compliance through a device-centric approach, which limits an administrator's scope into risky user behavior that exists within their organization.
With every user owning multiple devices a comprehensive risk view across all devices and users is required.
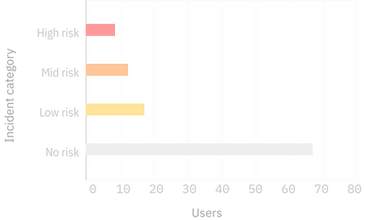
User Risk Management uses contextual information to detect risky conditions that compromise a security posture. It assesses risk based not only on the endpoint itself but also adds the more complex factors related to user behaviour and history across all of their devices. Users are evaluated for risk at regular intervals through a personalized Risk Model.
THE USER RISK MANAGEMENT SERVICE


SECURITY DASHBOARD, RISKY USERS & USER DETAILS
UEM is used to enforce restrictions, block or wipe risky devices. A risk score based on user behaviour allows the admin to apply granular controls over user entitlements. The model is customizable for each employee to accommodate the variability of what users need to stay productive and secure. The User Risk Management workflow consists of a Security Dashboard, Risky users dashboard, User Summary View, and Risk Rule Configurator (as seen in the below screen video). Administrators can view the risk in the organization with the Security Dashboard which includes an overview of the top risky users, risky devices, total risk incidents, and the average risk score across the organization. Administrators can drill-down to the Risky user dashboard and devices to get a comprehensive overview of the incidents committed by a single user with the user Summary View. With the Risk Rule Configurator, administrators can customize the risk model to identify the risk incidents according to their organization's needs.
THE IBM CARBON DESIGN SYSTEM

I have created the design based on detailed discussions with various stakeholders. We introduced a new design and UI framework. It's the first MaaS360 workflow designed from scratch using the Carbon Design System for IBM Security offerings.
A customer survey conducted post modrnization has following response ,


CUSTOMER SURVEY
Post beta release we conducted survey on more than 50 active customers of various sizes (Large, Medium, SMB., Small) and domains (Education, Health, Government, etc) . The conclusions statistics are as per below


EASY & SIMPLIFIED NAVIGATION
We introduced path-based breadcrumbs as a secondary navigation pattern. They enable the user to quickly move up to a parent level or previous step.
INTUITIVE
We used the perceptible batch filter, contrasting the rest of the portal. The batch filter works best when the user is making several filtering selections across different categories that may take a longer time to mentally process.
